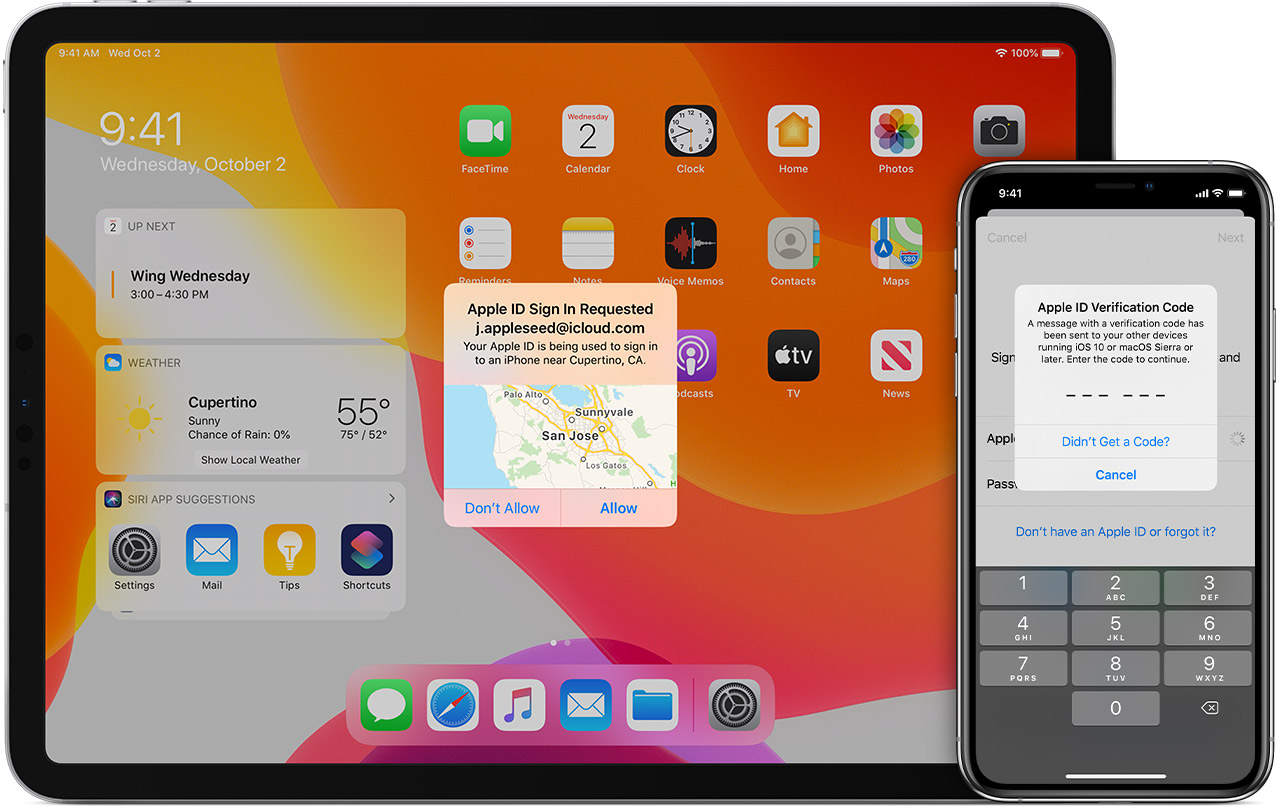
Two-Factor Authentication is an excellent process for adding extra security to accounts and devices. It has been playing a significant role in the field of security and protection of your details for several years. However, there are some ways also that can exploit this process to expose the accounts and devices that use it. Before setting up any Two-Factor Authentication solution, you should be aware of its advantages, strengths, disadvantages, and weaknesses.
Two-Factor Authentication has been adopted by several companies to secure their data and information from any kind of cyber attack. Nowadays, hackers have grown stronger with the advancement in technology, and to protect our accounts and devices, this Two-Factor Authentication process plays a crucial role. In this process, when you try to access an account or any device entitled with Two-Factor Authentication, the service will send a message to a device or authenticator software, and that must be inputted to grant access to that device or account. This process lowers the risk of an account being hacked.
There are other security solutions also available and being used by many companies along with this Two-Factor Authentication. It is because any Multi-Factor Authentication is much better than just setting up a password. However, Two-Factor Authentication is a standard security solution for many operating systems, devices, and third-party websites.
How Safe Is Two-Factor Authentication?
Two-Factor Authentication is not that much better as compared to the Multi-Factor Authentication process, which allows the user to utilize multiple forms of Authentication when they confirm their identity online. However, according to the information, there are more than 12 ways to breach Multi-Factor Authentication, and almost half of the cybersecurity breaches are not controllable by strong Multi-Factor Authentication.
One of the easiest ways to breach the Two-Factor Authentication is a phishing scam. Although this process can make your account more secure, certain phishing emails can be very tricky and can also expose your credentials along with the Two-Factor Authentication code. Even Multi-Factor Authentication cannot be prevented from hacking completely, such as client-side attacks, bugs, and old software that can be exploited easily. Therefore, Two-Factor Authentication is just one step to secure your account details and devices but cannot be considered as a complete solution.
However, using Two-Factor Authentication is far better and safer as compared to the standard password setup process. If we talk about this Two-Factor Authentication, it is not the only way that data should be protected. It is responsible for reducing the risk of having an account hacked.
source: Two-Factor Authentication