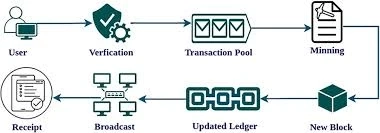
Decentralized applications (often called Apps) are becoming a practical option for organizations that require transparent recordkeeping, shared access between multiple participants, and verifiable transactions. Unlike conventional software, a decentralized application does not rely on a single central database. Instead, it operates on a distributed network where records are validated collectively and stored in an immutable ledger.
While the concept appears straightforward, building a secure decentralized application requires careful planning. Companies sometimes focus heavily on the technology itself and overlook governance, testing, and operational workflows. As a result, the platform may function technically but fail to support real business processes. To avoid these issues, many organizations consult experienced blockchain development Company uae and a capable blockchain development agency uae before starting development.
Below is a structured explanation of the essential steps involved in creating a secure decentralized application.
1. Defining the Business Objective
Every successful dApp begins with a clear purpose. Blockchain is not a universal replacement for traditional software. It is most effective when multiple stakeholders need to share and trust the same information without depending on a single authority.
During this stage, organizations identify:
- what problem they want to solve
- who will use the system
- what data needs verification
- whether decentralization actually adds value
For example, supply chain tracking, shared document validation, or multi-party approvals often benefit from decentralized systems. However, internal workflows handled by a single department may not require blockchain at all.
Establishing a defined use case prevents unnecessary complexity later in development.
2. Selecting the Appropriate Blockchain Network
After clarifying objectives, the next step is choosing the network structure. Not all blockchains operate the same way, and the selection affects performance, access control, and governance.
Public Networks:
Open participation, transparent records, but variable transaction speed.
Private Networks:
Controlled access, faster processing, and suitable for enterprise collaboration.
Consortium Networks:
Shared governance among selected participants, often used when multiple organizations cooperate.
Choosing the correct network early avoids redesign and ensures the system matches operational requirements.
3. Designing the System Architecture
A decentralized application consists of several components working together:
- smart contracts
- user interface
- wallet integration
- off-chain storage
- APIs for system communication
Architecture design determines how these elements interact. Some data is stored directly on the blockchain, while other information remains off-chain for privacy or efficiency reasons.
Careful architecture planning ensures scalability and maintainability. Without it, systems may face performance delays once user activity increases.
4. Developing Smart Contracts
Smart contracts are the operational core of a decentralized application. They define rules, automate processes, and execute actions when specific conditions are met.
Examples include:
- approving a document after verification
- releasing payment after delivery confirmation
- granting access when authorization is validated
Because smart contracts are difficult to change after deployment, they must be written with precision. Even a small logic error can interrupt operations or create security risks.
Development involves not only coding but also reviewing business logic to confirm that contract rules match real-world processes.
5. Implementing Wallet Integration
Users interact with the blockchain through wallets. A wallet signs transactions and confirms user identity within the network.
There are two primary models:
Custodial Wallets:
The platform manages keys for users, simplifying access.
Non-Custodial Wallets:
Users manage their own keys, increasing autonomy and responsibility.
The decision depends on the technical familiarity of users and the level of control required. Clear transaction prompts and understandable confirmation steps are necessary to ensure usability.
6. Security Testing and Auditing
Security testing is one of the most critical stages. Blockchain systems are secure by design, but vulnerabilities may arise from incorrect implementation.
Testing includes:
- code review of smart contracts
- vulnerability scanning
- penetration testing
- transaction simulation
Security audits confirm that transactions execute correctly and that unauthorized actions cannot occur. This stage significantly reduces operational risk after deployment.
7. Integration with Existing Systems
Most organizations already operate ERP platforms, CRMs, payment systems, and reporting tools. The decentralized application must connect with these systems to be useful.
Integration allows:
- automatic record synchronization
- reporting and analytics
- operational workflow continuity
Without proper integration, users may need to duplicate data entry, which reduces efficiency and discourages adoption.
8. User Interface and Experience Design
Technical reliability alone does not guarantee success. Users must understand how to use the platform comfortably. Transaction confirmations, approvals, and status updates should be clearly presented.
Effective interfaces provide:
- simple dashboards
- clear instructions
- visible transaction status
- understandable notifications
When users trust the interface, they trust the system.
9. Deployment and Network Configuration
Once testing is complete, the application moves to deployment. This includes:
- configuring network nodes
- assigning participant permissions
- setting transaction validation rules
Deployment also involves creating operational procedures, including user onboarding and system monitoring.
Organizations typically perform a controlled rollout, beginning with a limited user group before expanding usage.
10. Ongoing Monitoring and Maintenance
Launching the application is not the final step. Blockchain platforms require continuous monitoring to ensure reliability.
Maintenance activities include:
- updating nodes
- reviewing transaction logs
- monitoring performance
- addressing technical issues
Regular reviews help maintain system stability as user activity increases and operational requirements evolve.
Conclusion
Developing a secure decentralized application requires more than technical coding. It involves planning, governance design, user experience consideration, and continuous oversight. Organizations that approach blockchain carefully can gain transparent recordkeeping, reliable verification, and improved collaboration between stakeholders.
Working with experienced blockchain development specialists uae and a structured blockchain development agency uae helps businesses evaluate feasibility, design suitable architecture, and deploy systems that support real operational needs rather than experimental projects.
A decentralized application succeeds when technology aligns with business processes and user understanding.
CTA – UAE Contact
Companies planning to build or upgrade a decentralized platform can consult SISGAIN for technical guidance and implementation support.
Location: Dubai & Abu Dhabi, United Arab Emirates
Contact: Reach out to SISGAIN to discuss your decentralized application requirements and deployment planning.