Businesses have become so data-centric that the value of data and consumer behavior is way more than that of the entire app development business. There are as many attempts at data exploitation as they are for app development. Attackers are gaining pace and momentum and it is becoming ever so difficult for developers to stay clear of them.
One thing about attacking privacy is that the whole process of it is reactive. The attackers react to a certain program or set of codes or functionalities that the developers have built. If the building or developing process is taken good care of by modern methods, it becomes difficult for any malpractice to succeed.
How Should Android Developers Tackle Security Hazards?
Android does have its own set of security features and recommendations that help you stay safe in your structure. Despite that, the patterns are often anticipated and data is compromised. To fight against the threats, one must be aware of all the fundamental security practices as well as the features that the Google-owned platform offers. Knowing the right techniques can save you from all the vulnerabilities. Following are some key techniques and recommendations that can make things difficult for attackers to possess any serious threat to your app and your data.
Updated Services & Dependencies
Most apps depend on predefined codes stored in external libraries to perform some conventional tasks. This saves memory and simplifies the coding structure of the app. Keeping Google Play services updated is a popular recommendation and all apps in devices that have Google Play services should have updated dependencies. You can check here if your Google Play services on the device where the app is installed are updated or not.
Checking on the dependencies like all libraries, and SDKs are up to date should be done before deploying the app as well. You can use Android’s SDK manager to update Android’s own dependencies and to check updates on any third-party dependencies, check on their websites if they have issued any.
Caution with WebView
All apps have external links and most of them like to use their in-app browser to perform those navigations. Although Android reduces the in-app browser’s capabilities to avoid any ambiguity, developers still must be very careful in authenticating any outbound links and must curate a list of content they want to allow in the WebView. Under no circumstances should your in-app view navigate to an address that is not in your control. If you are not sure about having control over the WebView navigation, using JavaScript Interface Support is strongly recommended since JavaScript injection is a common malpractice among attackers. Another recommended method is to use the code celarCache() which clears any local storage of malicious files.
Safe storage of App Data
Your data is your biggest asset when it comes to handling devices. Apps usually store data in 3 different methods namely internal storage, external storage & content providers. For the most part of the data usage, the internal storage method is secure enough as the app stores all your usage data on its own internal storage that is only accessible to that particular app. In case of exchanging data with other apps, usage of content providers is recommended.
Files on external storage are more vulnerable as they are outside of the control of the app. In case of accessing a file from external storage, for any android app development service it is a recommended practice to perform input validation. General practice is to avoid storing any sensitive data like executable files or class files externally.
Content Providers
Sharing data among apps is a common phenomenon these days and ensuring the safety of your data amidst all this inter-app sharing can get a tad bit tricky. The standard practices to avoid any data theft include enforcing read-only or write-only accesses to the data, allowing one-time access, and using “content://” URI and not “file://” URI.
The content provider method to share data between the apps works on a structured storage mechanism that monitors the whole process. This encryption as mentioned earlier can be read/write-only, be a one-off thing, or can be marked as a regular instance for the system to allow future exchanges without any query.
Use & Create Permissions
Applications use permissions to perform tasks that are not defined in the sandboxes by Android. Usage of any hardware by any app requires such permissions. Developers rely heavily on having full control over the user’s device features to make the app experience intuitive. This comes with a high risk of attack. When it comes to permissions, less is more.
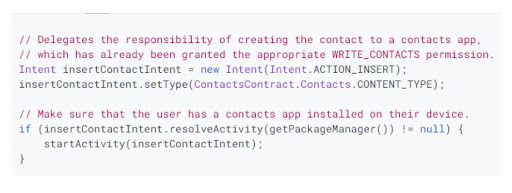
Most apps use intents to defer function, which essentially is referring to the native app that has all the permissions, instead of forming a new permission altogether. For any formation of new permissions, the standard signature protection level is used. These signatures are a secure and transparent method to perform tasks that require access outside the app. These signatures verify that the access is requested by the same developer and avoid any other attempt of access by any other app or developer. To declare new permission, the element is used in the manifest and to add more dynamism to it, addPermission() method is also used.
Image source: https://developer.android.com/topic/security/best-practices#java
The above example shows how to use intent to direct users to the contacts app instead of requesting read or write permissions.
Use of Cryptography
Cryptography is an advanced method of encrypting messages and exchanges with syntax that can neither be rewritten nor copied. This method has been around for a while and Android does provide its own set of functions to perform cryptographic encryption. There are recommended algorithms to come up with best cryptic encryption and it is widely recommended to specify Java Cryptography Architecture (JCA) providers if you are using Android’s Keystore system for cryptography to avoid any compatibility issues. There is a whole library of codes to perform cryptographic encryption to perform tasks like read, write, encrypting a message, generating a message digest, generating or verifying a digital signature, etc.
Conclusion
In the data-dominant digital business, fighting theft and spy attacks is getting more difficult with each passing day. While Android does have in-built functionalities that developers can use to fight any such attempts, it is down to the developers to make the right mix and combination of various techniques and functionalities to ensure the best safety of consumer data. Android does have a bag full of Armor apt enough to fight any modern-day attack but to be able to use it in its best merit requires experience and skill. To sum it up, using these tools and staying updated about both threats and functionalities offered to fight the threats can keep developers at least a couple of steps ahead of their attacker enemies.