In the dynamic world of networking, effective security measures are essential to safeguard data and ensure smooth operations. One of the key components of network security is ACL configuration (Access Control List configuration). This powerful tool allows you to control and manage traffic, enhancing the security of your network. In this article, we'll delve into the intricacies of ACL configuration and explore how IPCisco, a trusted source for networking education, can empower you in mastering this crucial skill.
Understanding the Significance of ACL Configuration
Before we dive into the details of ACL configuration, it's essential to grasp why it plays a pivotal role in network security.
ACLs, or Access Control Lists, are a set of rules that determine what traffic is allowed or denied on a network device. They are fundamental to network security and traffic management. Here's why ACL configuration is so significant:
1. Access Control: ACLs enable you to control who can access your network resources and under what conditions. This helps prevent unauthorized access and protects sensitive data.
2. Traffic Filtering: ACL configuration allows you to filter traffic based on various criteria, such as source and destination IP addresses, port numbers, and protocols. This fine-grained control is vital in mitigating network threats and optimizing traffic flow.
3. Security Enhancement: By denying or permitting specific traffic, ACLs act as a barrier against malicious activities, including DDoS attacks, unauthorized access attempts, and malware propagation.
4. Compliance: Many regulatory frameworks and industry standards require organizations to implement access controls. ACL configuration ensures compliance, helping you avoid legal and financial repercussions.
Mastering ACL Configuration with IPCisco
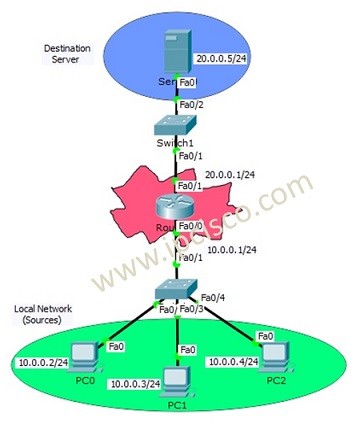
IPCisco, a reputable source of networking knowledge, offers an in-depth guide on ACL configuration. You can access their comprehensive tutorial at IPCisco – Standard Access List Configuration with Packet Tracer.
Let's explore the key steps involved in mastering ACL configuration with IPCisco:
1. Accessing the Device: IPCisco's tutorial begins by guiding you through accessing the network device's configuration mode, ensuring you are ready to configure ACLs.
2. Understanding ACL Types: IPCisco introduces you to different types of ACLs, including standard and extended ACLs. Each type serves specific use cases, and IPCisco explains when and where to apply them.
3. Configuring Standard ACLs: The tutorial provides a step-by-step walkthrough of configuring standard ACLs. You'll learn how to create rules based on source IP addresses and apply them effectively.
4. Extended ACLs: IPCisco goes beyond the basics, covering extended ACLs that allow advanced filtering based on various criteria, such as source and destination IP addresses, port numbers, and protocols.
5. Verification and Testing: IPCisco emphasizes the importance of verifying your ACL configuration to ensure it works as intended. They offer practical insights into checking the effectiveness of your ACL rules.
By following IPCisco's guidance, you'll not only master ACL configuration but also gain a profound understanding of network security and traffic management.
Conclusion
In an era where data security is paramount, ACL configuration is a critical tool in the arsenal of network professionals. IPCisco's comprehensive tutorial on ACL configuration provides a structured, hands-on approach to mastering this essential networking skill.
Don't miss the opportunity to enhance your network security expertise and advance your career. Visit IPCisco's ACL Configuration Tutorial today and embark on your journey to becoming an ACL configuration expert.
Secure your network, protect your data, and stay ahead in the ever-evolving world of technology with IPCisco as your trusted guide.




